The recent surge in phishing attacks capable of bypassing multi-factor authentication (MFA) has raised significant concerns in the cybersecurity landscape. These attacks highlight the fact that even systems protected by MFA have vulnerabilities, making it imperative for organizations to stay vigilant and not rely on a single control as a silver bullet.
One such campaign, known as 0ktapus, provides a crucial case study in understanding the methods and impacts of these phishing attacks. Over the past few years, 0ktapus has successfully launched campaigns against large organizations, including players in the cryptocurrency space.
This article delves into the anatomy of an Okta-based phishing campaign encountered by Fireblocks’ security operations team, showcasing how low-skill, low-effort methods are leveraged by adversaries into highly effective campaigns. We’ll then explore mitigation strategies and techniques you can employ against such attacks.
We have confirmed that no Fireblocks employees or credentials were compromised in the 0ktapus campaign against Fireblocks, and the entire campaign was stopped in its tracks within 2 hours of initiation.
What is 0ktapus and who’s behind it?
Scattered Spider, also referred to as UNC3944 and Scatter Swine among other names, is a group known for launching hacking campaigns heavily utilizing phishing via SMS and Telegram, as well as social engineering through popular cloud and identity platforms such as Okta. One of its most successful campaigns as of yet, codenamed 0ktapus by group-IB researchers, has resulted in thousands of leaked credentials and over 130 organizations being compromised worldwide. 0ktapus has recently seen a resurgence because of its simplicity, and the fact many organizations are still prone to the techniques that made the campaign successful in the past.
Attack lifecycle and deep-dive
The way 0ktapus phishing campaigns operate, while simple in their nature and sophistication, is highly polished and effective.
In the course of the attack, the actor chooses organizations that utilize the IAM/IdP platform Okta. It then targets those organizations’ employees via specially-crafted smishing (SMS-based phishing) messages. The text messages will often contain a call to action with a sense of urgency, alongside a link to a URL that will typically impersonate the targeted organization’s SSO/IdP page.
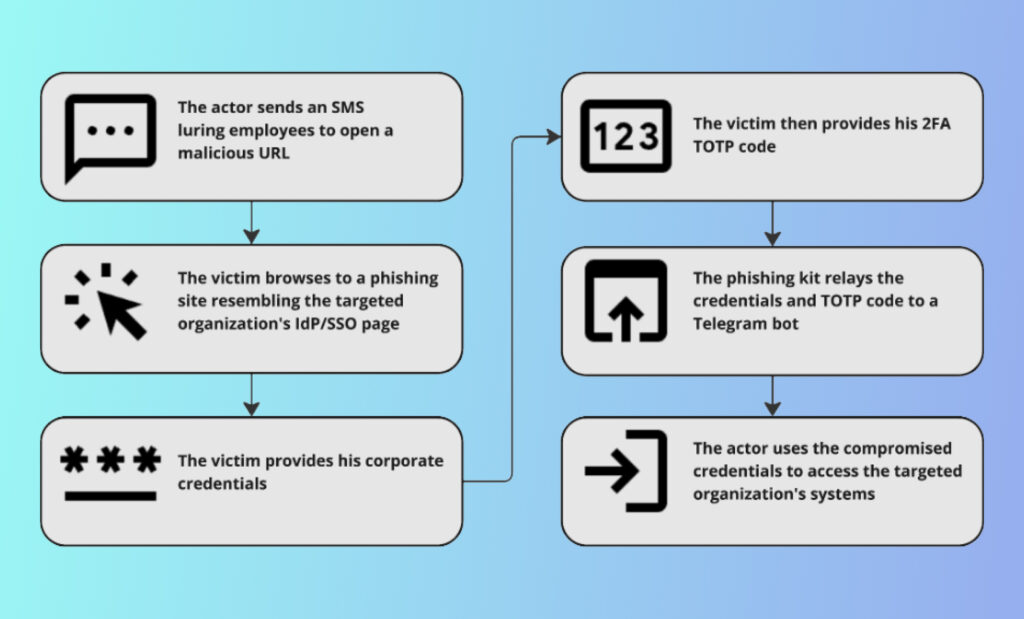
One of the focal points in this campaign, outside of its scale and relative success, is utilizing SMS as a delivery mechanism for malicious URLs instead of traditional email-based phishing. This mechanism allows attackers to deliver malicious URLs while circumventing traditional enterprise security solutions, such as mail gateways and web security solutions, yet not significantly impacting the likelihood of victims interacting with the phishing kit.
Initial Phishing Attempt
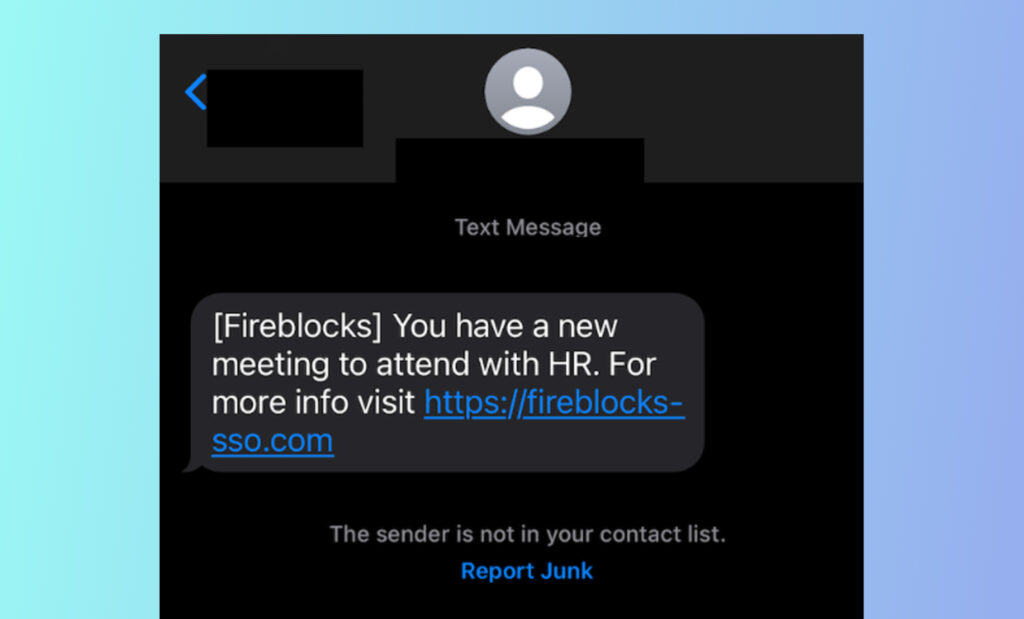
The 0ktapus campaign against Fireblocks began with a series of well-crafted phishing SMS messages from US-based phone numbers, mimicking legitimate communications from Fireblocks. The messages urged recipients to visit a link in order to attend a meeting with HR, redirecting them to a counterfeit Okta login page. The attackers used domain spoofing and lookalike URLs to enhance the authenticity of their phishing campaigns, a tactic that has proved effective in past instances.
Credential harvesting and MFA bypass

Upon clicking the URL, victims would be lured to a counterfeit OKTA login page. The phishing site included in the phishing kit was designed to look nearly identical to the real Okta login portal, making it challenging for users to recognize the deception. The URLs to the phishing site will typically contain words such as the company’s name, “SSO”, “OKTA,” and “IdP” in order to add to their legitimacy. Once the victims enter their credentials on the imposter Okta page, the phishing kit will immediately prompt the user to provide his one-time 2FA token. After providing the valid credentials, the phishing kit would immediately relay the information to a Telegram bot, which the attackers would monitor in real time in order to use the credentials before their expiration (this had to be done before the TOTP token expires, which typically takes30 seconds).
From this point on, with valid credentials and stolen tokens, the attackers could infiltrate sensitive systems and data. Considering the success this campaign has had against large companies in the past, we can assume that this type of attack is still valid against most organizations, and can be highly successful against organizations employing this type of SSO setup.
A recap of the incident and how Fireblocks handled it
Within 30 minutes (or less) of the actor registering the malicious domain, our threat hunting team received indicators for the domain’s registration, immediately requesting a takedown for the domain in parallel to our security operations team and issuing company-wide communications to ensure no employees had interacted with the malicious URL. We were able to confirm no credentials were compromised, and no employees interacted with the malicious web page outside of our security personnel. In under 2 hours of launching the campaign and upon identifying our efforts to derail it, the actor took down the phishing kit and rendered the webpage benign. Since then, the domain has been removed following takedown requests from our security team.
In addition, Fireblocks employs FIDO2-compliant and WebAuthn-compliant authentication and conditional-access measures, which prevents an attacker from getting past the credential entry phase via a campaign such as this.
How to protect yourself and your business
Here are some guidelines for preventing an attack like this from being successful against your team or organization:
1) Strengthening MFA Implementation
While MFA is critical, it must be fortified with additional security layers. Implementing FIDO-2 and WebAuthn compliant authentication and biometric verification can significantly reduce the risk of MFA bypass through phishing. We would recommend aiming at phishing-proof mechanisms unless production constraints prevent their implementation.
2) Conditional Access and Network Restrictions
To reduce the effectiveness of credential re-use, credential stuffing, and phishing, it’s important to not only rely on authentication mechanisms as security layers. Condition-based checks, such as device fingerprinting, IP restrictions and host checks, reduce the ability of attackers to arbitrarily use stolen credentials or bypass access security layers.
3) Enhancing User Training and Awareness
Regular training sessions are crucial for educating employees about phishing attacks. Users should be trained to recognize suspicious messages of all types – emails, SMS and others, and encouraged to report them immediately. Providing easy-to-use reporting tools can enhance this process. Simulated phishing exercises can also be conducted to test and improve employee awareness and response to phishing attempts. We also recommend positively reinforcing employees’ good behavior and vigilance with positive acknowledgement.
4) Leveraging Threat Intelligence and Threat Hunting for Rapid Response
Robust detection solutions are necessary to adequately respond to phishing campaigns. Implementing threat hunting and threat intelligence capabilities to detect typosquatting, imposter domains, and phishing attacks can provide great value in stopping campaigns in their tracks before propagating to a large set of users or escalating into an incident. Being prepared with detailed playbooks, communication plans, and escalation plans for any incident can further win back precious time as events unfold.
5) Regular Security Audits
Conducting regular security audits helps identify and rectify vulnerabilities within your systems. Proactive assessments ensure that defenses are up-to-date, uniformly deployed and capable of countering emerging threats. Penetration testing and posture assessments should be performed regularly to simulate potential attack vectors and improve overall security posture.
Modern phishing attacks targeting Okta and similar identity management platforms remain a significant threat to organizations. The 0ktapus campaign exemplifies how even basic social engineering techniques could bypass MFA and compromise even large and mature organizations. By understanding these attack vectors and implementing best practices, organizations can enhance their defenses and safeguard their digital assets. Staying vigilant and proactive in cybersecurity strategies is essential to mitigate the evolving landscape of cyber threats.
Watch our ‘Becoming a Cybersecurity-First Organization’ session to learn additional tips and tricks on how to build an effective security program.