Introduction
As of January 17th, 2025, full compliance with DORA (the Digital Operational Resilience Act) and its technical standards is required for financial institutions and other regulated entities in the EU.
DORA is an EU regulation that looks to ensure that financial services can withstand and recover from disruptions related to technology, such as cyberattacks or system failures. It does so by setting out clear guidelines around areas like risk management, incident reporting, and collaboration with third-party providers. DORA is aimed at safeguarding the European financial sector so that it can continue to function smoothly in the face of cyber threats and disruptions. At the same time, it intends to foster trust in the EU financial system.
For stakeholders (like security, compliance or legal teams) at regulated entities servicing crypto assets or acting as crypto asset intermediaries, the onset of DORA may be a daunting prospect. While the regulations promise a new era of operational resilience for the EU financial sector, they also ask institutions to rethink certain aspects of their current workflow – potentially an intimidating undertaking. But with a degree of preparedness, along with collaboration with the right set of critical partners, we at Fireblocks believe EU institutions can adhere to these new regulations while continuing to thrive.
Read on to learn more about what DORA requires, and review our recommendations for managing DORA compliance effectively.
Understanding DORA
DORA requires Crypto Asset Service Providers (CASPs) and licensed financial institutions to manage and mitigate risks linked to their Information and Communication Technology (ICT) infrastructure. It sets out clear guidelines on how these institutions should prepare for and respond to potential technology failures or attacks, including:
- Risk management: Institutions need to assess, monitor, and manage digital risks (like cybersecurity threats).
- Incident reporting: Institutions must report significant digital incidents to regulators.
- Testing and recovery: Regular testing of systems and having recovery plans in place is required to ensure continued service during disruptions.
- Third-party providers: Institutions bear the full responsibility for their usage of ICT third-party service providers, and must verify the appropriateness of those parties’ security and operational resilience.
- Information sharing: Institutions must promote collaborative information sharing practices to improve resilience across the industry.
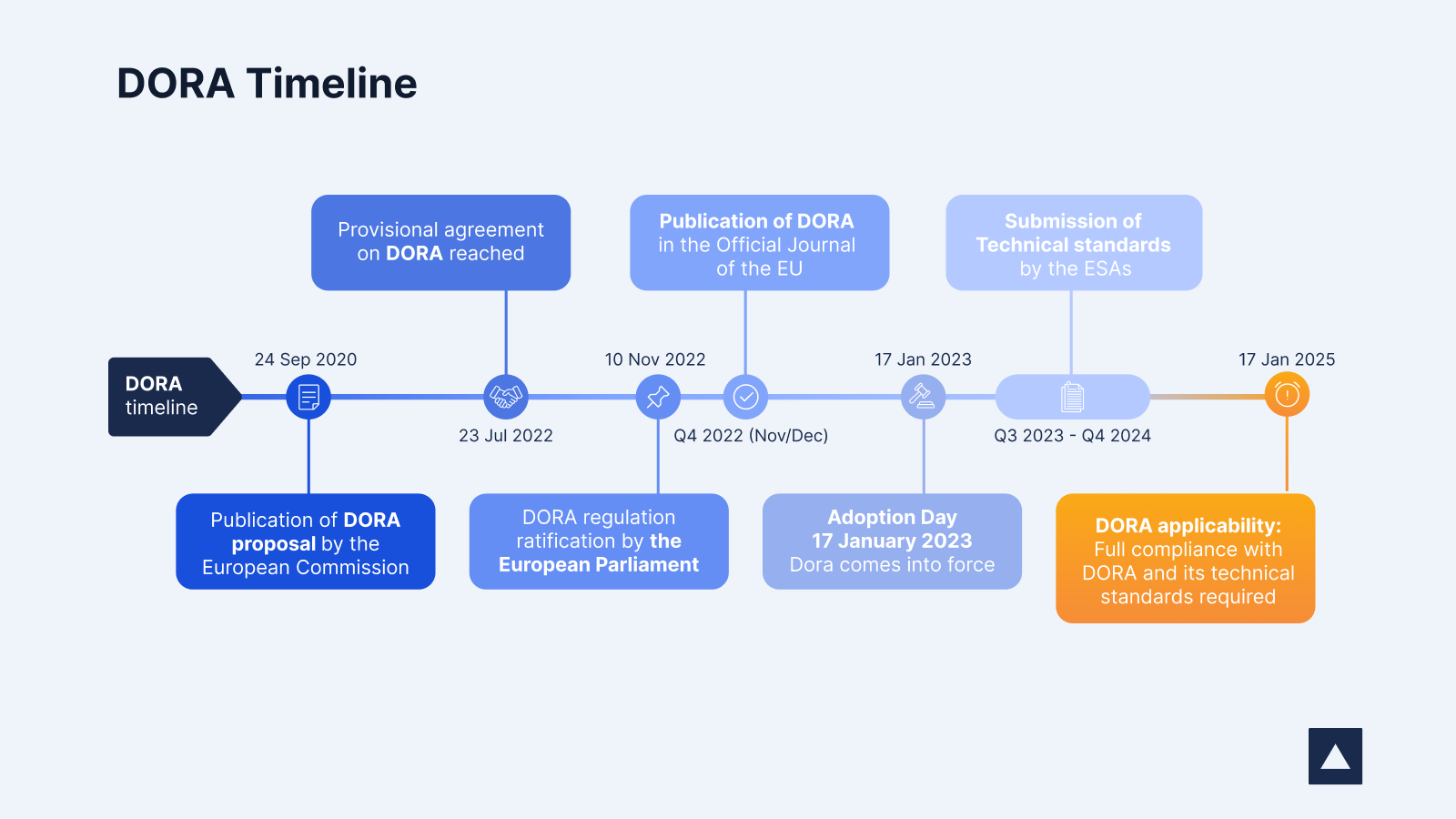
Timeline
DORA first came into force on January 17, 2023. Full compliance is required as of January 17, 2025.
Institutions that fail to comply with DORA’s requirements may face enforcement actions, including fines, sanctions, or restrictions on their operations.
Deep Dive into Third-Party Risk Management Under DORA
While all aspects of DORA are important to understand, the third-party risk management pillar of the regulation is critical since it relates to factors external to the regulated entity. You may be asking: what should you expect from your ICT third party providers supporting a critical or important function, and what’s the depth of understanding you should have?
First, it’s important to note that while your organization may depend on a large number of third party vendors, suppliers and contractors, not all of them are equally important to your digital and operational resiliency. On most occasions only a relatively small fraction are supporting critical or important functions, for which extra care is required under DORA. These will most likely be providers of ICT Infrastructure (Compute, Network, Security) and some of your business’s core applications providers such as CRM, ERP and, of course, mission-critical financial and operational systems.
As you consider which third parties support critical or important functions, it’s imperative to choose partners that are capable of operating at standards that are aligned with DORA regulations and the accompanying RTS relevant to third party risk management (TPRM). TPRM can be divided into 4 subpillars: due diligence, contractual agreements, monitoring & review, and exit strategies.
Due Diligence
Due diligence refers to the process by which institutions assess and evaluate the risks associated with third-party ICT providers, both before entering into any contractual relationship, and continuously during any engagement. DORA asks institutions to conduct thorough risk assessments to avoid relying on third-party providers that could jeopardize the institution’s operational resilience.
Institutions must assess the potential operational, security, financial, and compliance risks associated with each third-party provider. They must also ensure that the proposed provider meets applicable regulatory requirements, including those related to data protection, cybersecurity, and business continuity.
Financial institutions must evaluate the cybersecurity measures of the third-party provider, and make sure its risk management, cybersecurity and operational resilience measures are adequate and appropriate to the associated risk profile.
Contractual Agreements
Contract management is a key area under DORA for establishing clear, legally binding agreements that protect the financial institution’s operational resilience in the event of disruptions and in light of the risks associated with third-party ICT providers.
Financial institutions must ensure that their contracts with third-party providers include provisions that specifically address ICT resilience and risk management. Some key provisions include SLAs that outline the required performance standards for the third party, security and incident management obligations, business continuity and disaster recovery provisions, and audit rights.
The contract with the third-party provider should also include detailed exit clauses that outline the steps to take in the event the relationship needs to be terminated or ended prematurely. These clauses should address transition and migration plans, data retrieval options, continuity of service, and notification requirements.
Monitoring and Review
Due diligence is not a one-time event. DORA requires financial institutions to continuously monitor and assess the performance and resilience of their third-party providers. Regular reviews should include monitoring service-level performance, security incidents, and compliance with agreed-upon terms. Financial institutions should reassess third-party risks whenever there are significant changes to the provider’s operations, such as mergers, acquisitions, or operational changes.
Institutions may employ various monitoring and assessment tools on their ICT third-party providers, which include audits performed by them or on their behalf, self-audits performed and reported on by the providers, certifications and other relevant information provided by the third parties, including periodic or regular reporting. However, institutions should not rely over time on just the third parties’ certifications and reports; the regulated entity must review and thoroughly assess this reporting, and must always ensure that it has the right to conduct its own individual or pooled audits.
Exit Strategies
Exit strategies are essential for ensuring that financial institutions can sever relationships with third-party ICT providers without risking service disruptions or operational failure. DORA emphasizes the need for clear exit strategies, particularly for critical third-party relationships.
Fireblocks as an ICT Service Provider Supporting a Critical Function and DORA Compliance
As a world leader in the digital asset management space, Fireblocks’ software-as-a-service technology enables thousands of customers to self-custody and manage their digital asset holdings. In most use cases, Fireblocks is considered an ICT provider supporting a critical or important function and has therefore taken steps to be well-prepared in terms of its security posture. Some of Fireblocks’ core advantages are:
- Fireblocks has developed – and has been maintaining for years – its mature information security management system (ISMS). This system adheres to industry standards and best practices, and covers all major security processes, including: risk management, identity and access management, secure software development lifecycle, incident response, security awareness program, and security testing. In order to facilitate “out-of-the-box compliance” for its customers, Fireblocks made the necessary amendments to its processes to make sure they adhere to the strictest expectations based on DORA.
- Fireblocks security is being continuously assessed and tested by accredited and vetted leading third parties, including SOC2 Type II by a “Big Four” audit firm, ISO standards certification (27001, 27017, 27018 and 22301), CCSS Level 3 QSP certification, external penetration testing, code reviews, and risk assessments. These external audits validate and verify the quality and effectiveness of Fireblocks’ processes and solutions.
- Fireblocks has in place a robust Business Continuity program (or “BCP”) which covers technological, human, geographical and other aspects of its business. This program includes business continuity, disaster recovery and crisis management plans, which are all regularly reviewed and tested. Particularly, the ISO-22301 standard for Business Continuity Management has been recently achieved in order to strengthen Fireblocks’ approach towards operational resiliency through its BCP.
- Fireblocks has developed a DORA-specific reporting scheme, which allows its customers to conduct their own review of the Fireblocks security efforts. This includes, amongst others:
- Annual reports and certifications on its ICT Security, Business Continuity and Emergency Plan measures.
- Periodic reporting on its ICT Security, ICT Service and Support levels.
- A Security Pooled Audit event during which customers get a deep-dive view into Fireblocks security, exclusive ICT security insights, and also engage with senior Fireblocks security personnel.
This reporting framework is designed in alignment with DORA obligations, to provide customers with the necessary information to assure them of Fireblocks’ level of security and operational resilience, while fulfilling their due diligence requirements in overseeing Fireblocks as an ICT third party provider.
Fireblocks has all of these security efforts bound into its Cyber & Operational Resilience compliance package, and reflected in its DORA regulatory addendum, which is now available for customers.
Conclusion
DORA is a landmark regulation that plays a pivotal role in strengthening the digital resilience of the EU financial sector. By adhering to DORA requirements, institutions safeguard their operations, protect customer data, and ensure continuity of critical services, all while reducing the systemic risks posed by third-party dependencies.
Ultimately, third-party vendor management under DORA not only minimizes the risks associated with external dependencies, but also contributes to the broader stability and integrity of the financial system. By enforcing these stringent requirements, DORA empowers institutions to reduce systemic risk, enhance their resilience to ICT threats, and better protect their customers and stakeholders in an increasingly interconnected and technology-driven financial landscape.
Disclaimer: This is not intended to provide legal advice and Fireblocks encourages you to conduct your own analysis (including seeking independent advice) with respect to the scope/applicability of DORA to your business or operations.